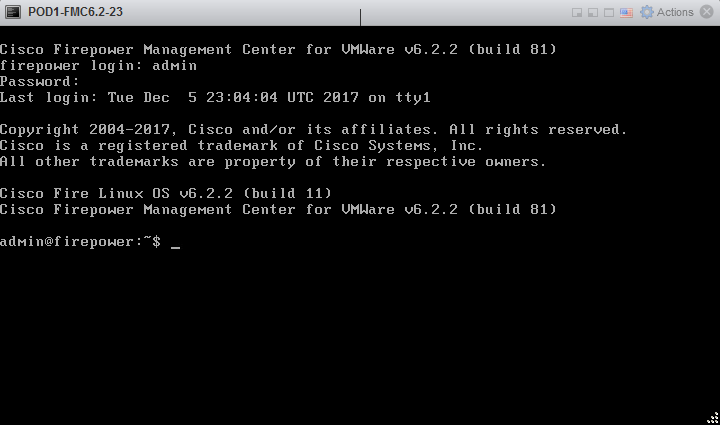
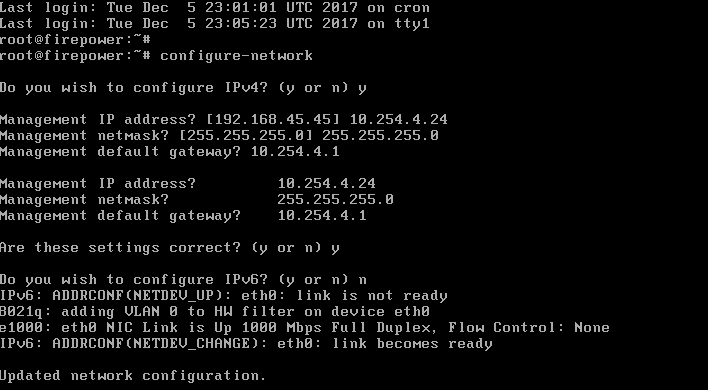
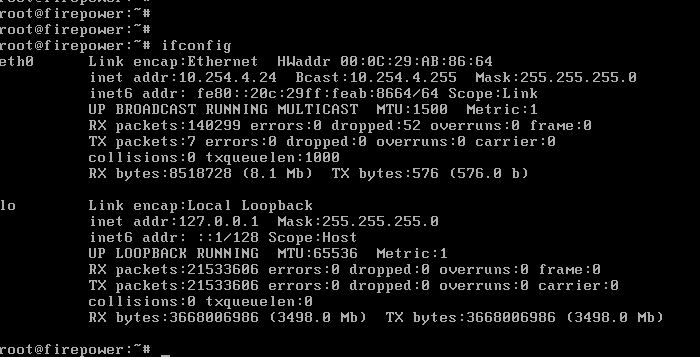
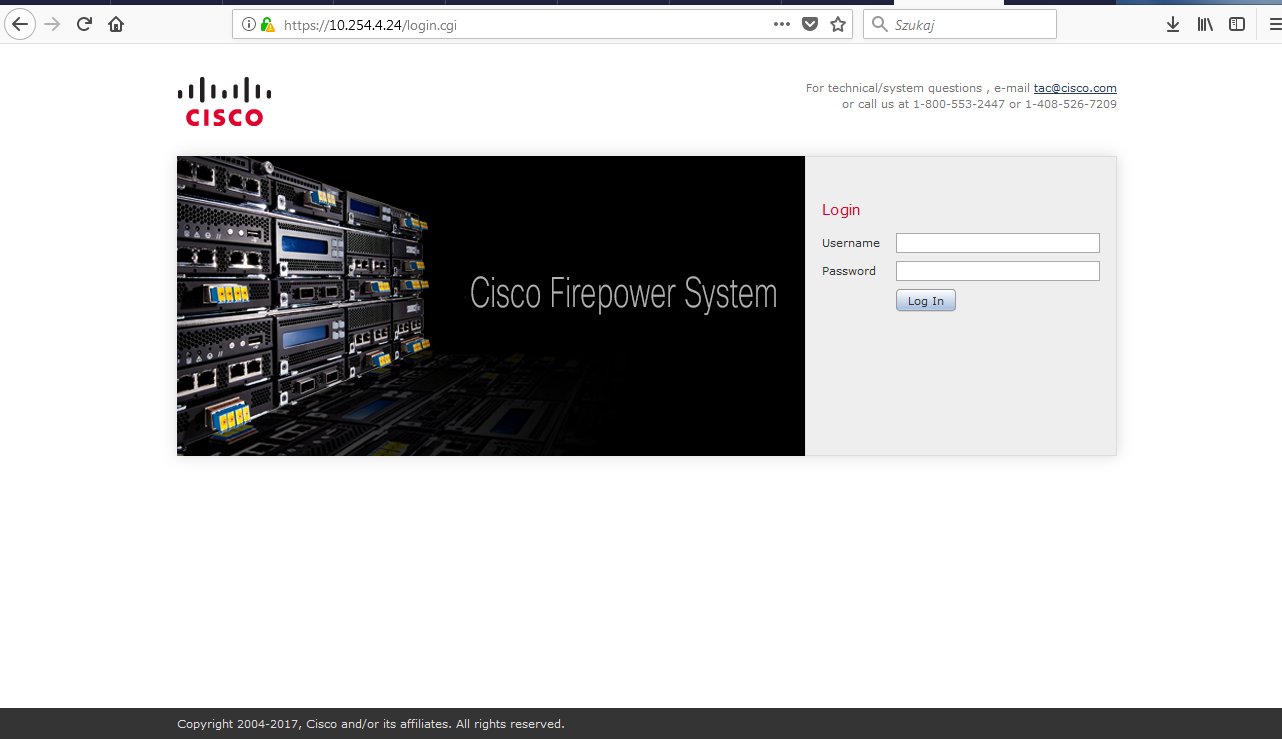
First of all, we have to create an SSID profile. You can do this with the command dot11 ssid ssid. Let’s make a SSID with the name ‘CiscoTalkWireless’.
|
1
2
|
ap(config)#dot11 ssid CiscoTalkWirelessap(config-ssid)# |
Next, we can configure the SSID properties. In this example, we want to use open authentication with key management provided by WPA2. In addition, I want to broadcast this SSID. This makes its easier for users to connect to your network. This is especially useful for guest wireless networks. While in SSID configuration mode:
|
1
2
3
4
|
ap(config-ssid)#authentication openap(config-ssid)#authentication key-management wpa version 2ap(config-ssid)#guest-modeap(config-ssid)#wpa-psk ascii CiscoTalkTutorials! |
The configuration is pretty self-explanatory.
authentication open enables open authentication.
authentication key-management wpa version 2 configures this SSID to use WPA2. If you leave off version 2and enter authentication key-management wpa, you are configuring the SSID with WPA.
guest-mode enables SSID broadcasting.
wpa-psk ascii sets the pre-shared key for the SSID.
Now with the SSID profile configured, we need to specify an encryption method. Let’s enter interface configuration mode on Dot11Radio0:
|
1
2
|
ap(config)#interface Dot11Radio0ap(config-if)# |
There are a few options you can use for encryption. You can also use AES, TKIP, and WEP. I strongly advise against using WEP and recommend AES over TKIP.
For AES:
|
1
|
ap(config-if)# encryption mode ciphers aes-ccm |
For TKIP:
|
1
|
ap(config-if)# encryption mode ciphers tkip |
Now with the encryption method in place, let’s assign the SSID:
|
1
|
ap(config-if)# ssid CiscoTalkWireless |
By default and as a security measure, all new Cisco Access Points ship with the radios turned off. So as a final step, let’s enable the radio:
|
1
|
ap(config-if)# no shutdown |
By default, Cisco access points select the least congested wireless channel. As soon as you enable the interface, the access point will scan and assign itself an appropriate channel. Once the channel selection process is complete, you should now have a working wireless network! You can verify connected clients by using the show dot11 associations command:
|
1
2
3
4
5
6
7
8
9
|
ap#show dot11 associations802.11 Client Stations on Dot11Radio0:SSID [CiscoTalkWireless] :MAC Address IP address Device Name Parent State100b.bbbd.e248 10.10.83.110 ccx-client CiscoTalk-PC self Assocap# |
My next post will be a tutorial on how to configure multiple SSIDs using different VLANs on a single access point.