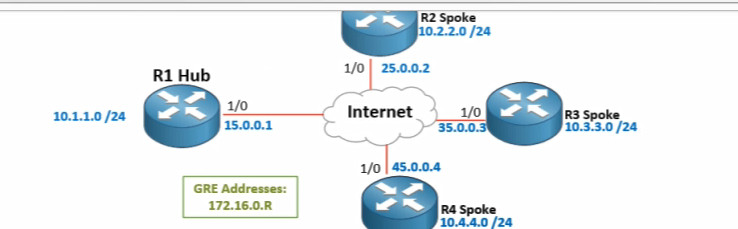
Simply make a batch file in windows and read from your excel file then convert the your datasheet to fortigate rules. In this code, I converted the excel file with 5 columns to the fortigate policy.
My Excel File:
any,any,ctldl.windowsupdate.com,80/443,Test1
any,any,microsoft.com,80,Test2
any,any,crl.microsoft.com,80,Test3
any,any,ssl.google-analytics.com,443,Test4
My Batch file:
@echo off
setlocal ENABLEDELAYEDEXPANSION
>output-configuration-policy.txt (
echo:config firewall policy
set /a Counter=1
for /f “tokens=1-5 delims=,” %%A IN (C:\Users\rules.txt) DO (
echo edit !counter!
echo set name %%E
echo set srcintf vlan910-1135
echo set dstintf vlan1000-1135
echo set srcaddr %%A
echo set dstaddr %%C
echo set action accept
echo set service “HTTPS” “HTTP”
echo set schedule “always”
echo set logtraffic all
set /a counter=!Counter! + 1
echo next
)
:end
echo:end
)
I have added counter to count from 1 to number of your rules.