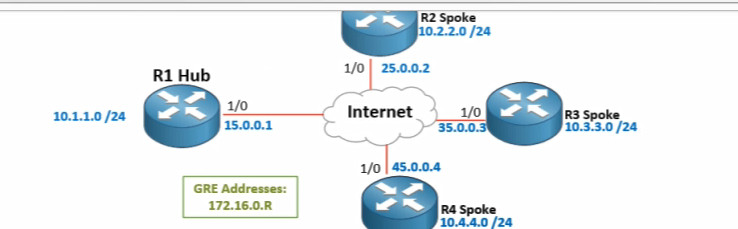
R1
int tunnel 0
tunnel source gi1/0
tunnel destination mode gre multipoint
tunnel key HRT //should be the same
ip nhrp network-id 1 //should be the same
ip nhrp authentication cisco123 //should be the same
ip nhrp map multicast dynamic
ip nhrp shortcut //phase 3
ip nhrp redirect //phase 3 – we write it in the server
ip address 172.16.0.1 255.255.255.0
tunnel path-mtu-discovery
ip tcp adjust-mss 1360
R2
int tunnel 0
tunnel mode gre multipoint
tunnel source gi 1/0
tunnel key HRT
ip nhrp network-id 1
ip nhrp authentication cisco123
ip nhrp shortcut
ip nhrp nhs 172.16.0.1
ip nhrp map 172.16.0.1 15.0.0.1 //Gre interface then IP interface
ip nhrp map multicast 15.0.0.1
ip address 172.16.0.2 255.255.255.0
ip tcp adjust-mss 1360
R3
int tunnel 0
tunnel mode gre multipoint
tunnel source gi 1/0
tunnel key HRT
ip nhrp network-id 1
ip nhrp authentication cisco123
ip nhrp shortcut
ip nhrp nhs 172.16.0.1
ip nhrp map 172.16.0.1 15.0.0.1 //Gre interface then IP interface
ip nhrp map multicast 15.0.0.1
ip address 172.16.0.3 255.255.255.0
ip tcp adjust-mss 1360
Configuring IPSEC on Each router
R1
————————-
(config)# crypto isakmp policy 5
(config-isakmp)# hash sha
(config-isakmp)# authentication pre-share
(config-isakmp)# group 14
(config-isakmp)# lifetime 86400
(config-isakmp)# encryption aes 256
(config)#crypto isakmp key cisco123 address …..(your device)
(config)#crypto ipsec transform-set OUTSET esp-aes 256 esp-sha-hmac
(cfg-crypto-trans)# mode transport
(config)#crypto ipsec profile OUR_IPSEC_PROFILE
(ipsec-profile)# set transform-set OURSET
(config)#int tunnel 0
(config-if)# tunnel protection ipsec profile OUR_IPSEC_PROFILE
show dmvpn
show crypto isakmp sa detail
show dmvpn peer nbma …..(IP Peer) detail
Troubleshooting
show run int tunnel 0
debug crypto isakmp // debug phase 1
show crypto isakmp policy
show crypto isakmp key
show crypto engine connections active
show dmvpn detail


